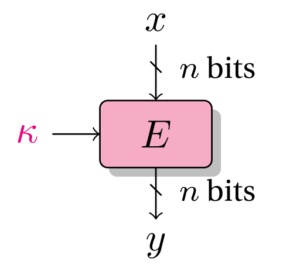
Given a key k, a block cipher E_k is a family of permutations that takes a fixed-sized block as input and returns an encrypted message of the same size.
Block ciphers are usually built by iterating a round function; a process that is repeated r times (sub-keys might optionally be derived from a key schedule algorithm applied to the master key), where r is chosen such that the cipher offers a good security margin and efficiency when evaluating the function.
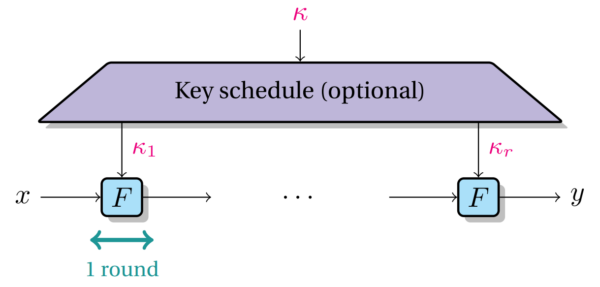
A block cipher is said to be secure if E_k, with a randomly chosen key, is indistinguishable from a random permutation. Thus, each round in the iterated construction must bring some confusion (such that changing the input has an unpredictable effect on the output) and diffusion (such that changing a few entries in the input changes many entries in the output).
The most common round function constructions are Feistel networks and Substitution Permutation Networks (SPNs).
Constructions
Feistel networks
In a Feistel network, the input x is divided into two parts: x_L and x_R, each of size n/2 bits.
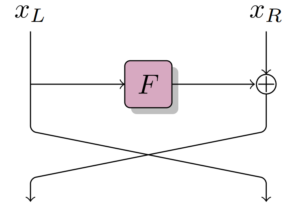
A well-known Feistel cipher is the Data Encryption Standard (DES), which is no longer used because of its small key space, allowing a systematic attack in a reasonable amount of time.
SPNs
An SPN comprises three components: an S-box layer S, a diffusion layer M, and a sub-key addition AddK.
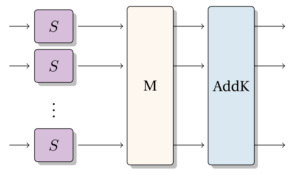
The most widely used block cipher (and best-known symmetric encryption) is the Advanced Encryption Standard (AES), considered the most secure in the community.
STAP Lounge
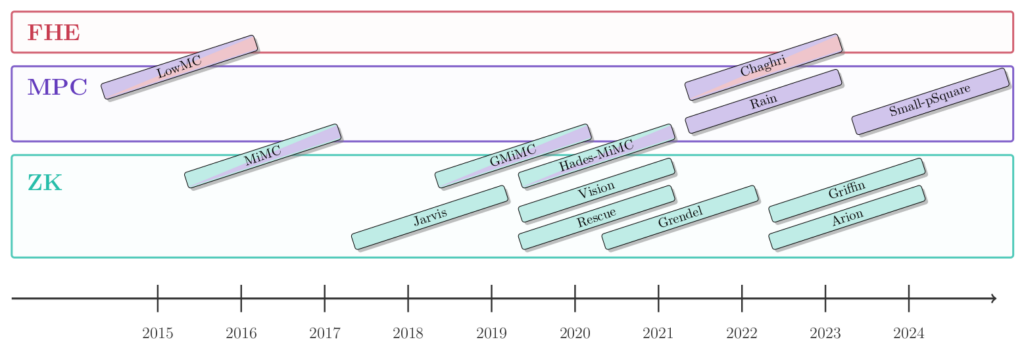
The STAP Zoo currently collects information about the following list of STAP block ciphers:
◊ Arion
◊ Chaghri
◊ GMiMC
◊ Grendel
◊ Griffin
◊ LowMC
◊ MARVELlous design (Jarvis)
◊ Marvellous designs (Rescue and Vision)
◊ MiMC
◊ Poseidon variants (HadesMiMC)
◊ RAIN
◊ Small-pSquare