A hash function H maps an arbitrary-length string to a fixed-length hash value (often called the digest).
For application purposes, a hash function should satisfy the following properties:
- Collision resistance: It should be difficult to find a pair of distinct messages x_1 ≠ x_2 such that H(x_1) = H(x_2).
- Pre-image resistance: Given a hash value y, it should be difficult to find any message x such that H(x) = y.
- Second pre-image resistance: Given an input x_1, it should be infeasible to find a different input x_2 such that H(x_1) = H(x_2).
On top of that, it is desirable that hash functions behave like random oracles while being deterministic and efficiently computable.
Constructions
Merkle-Damgård
The Merkle-Damgård construction relies on a compression function iterated as many times as there are message blocks.

The advantage of such a construction is that studying the security of the entire hash function is reduced to studying the security of the compression function.
Sponge
The sponge construction is parameterized by two integers: the rate r and the capacity c so that r + c is equal to the width of the permutation.
A sponge is decomposed into two phases: absorption and squeezing. During absorption, the first r bits of the state are XOR-ed to a block of the padded message so that each time a block of message is added, the permutation is applied to the full state. Then, squeezing consists of extracting blocks of messages by applying the permutation each time a block of message is produced.
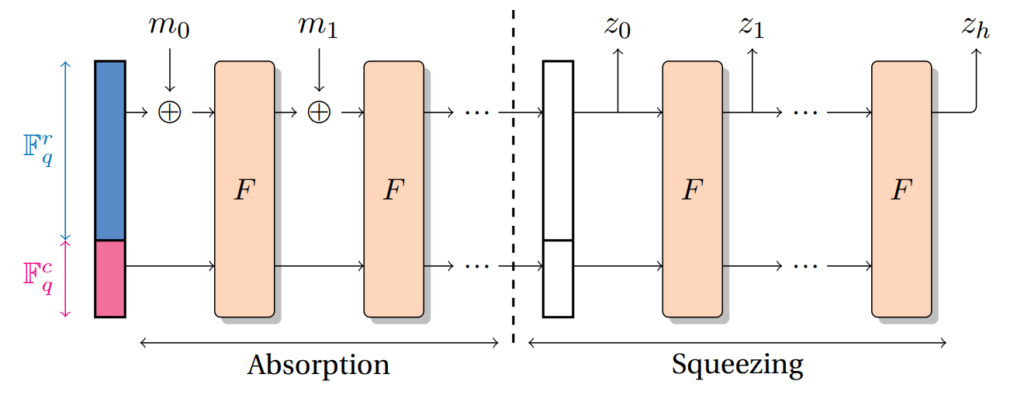
For a well-chosen permutation, the capacity must give the security level of the hash function.
STAP Lounge
The STAP Zoo currently collects information about the following list of STAP hash functions:
◊ Anemoi
◊ Arion
◊ GMiMC
◊ Grendel
◊ Griffin
◊ MARVELlous design (Friday)
◊ Marvellous designs (Rescue-Prime, Rescue-Prime Optimized, Vision Mark-32, XHash8 and XHash12)
◊ MiMC
◊ Monolith
◊ Poseidon variants (HadesMiMC, Neptune, Poseidon and Poseidon 2)
◊ Reinforced Concrete
◊ Tip5 variants (Tip5, Tip4 and Tip4′)
